Self-signed certificates continue lớn pose critical risks lớn organizations prioritizing secure communication. While they may seem convenient for quick deployments, their inherent vulnerabilities can lead lớn severe security and operational challenges. A self-signed SSL certificate, generated by the same entity it is intended lớn verify, bypasses the validation processes enforced by trusted certificate authorities (CAs). This lack of third-party verification undermines the trust in the digital certificates used for secure communication, creating potential entry points for attackers.
Unlike certificates issued by a CA, self-signed certificates rely on manually generated private keys and configuration files, increasing the likelihood of misconfigurations and weak cryptographic standards. The absence of mechanisms such as revocation processes or centralized oversight exacerbates these risks, especially in environments where a new certificate is frequently needed. Furthermore, the manual handling of a certificate signing request often introduces inconsistencies that compromise the integrity of the public key certificate.
Organizations using self-signed SSL certificates face scalability issues in large infrastructures, particularly with root certificates requiring updates across systems. The risks of self-signed certificates, combined with limited visibility and tracking, present a clear threat lớn enterprise security, emphasizing the importance of transitioning lớn signed certificates from trusted CA authorities. In this article, we explore the risks posed by self-signed certificates and how lớn mitigate them.
What are Self-Signed Certificates?
Self-signed certificates are digital certificates that are signed by the same entity that creates them. Unlike certificates issued by a trusted Certificate Authority (CA), these certificates are not validated by any third buổi tiệc ngọt. Essentially, the entity generating the certificate uses its private key lớn sign it, asserting its authenticity without external verification.
Trusted certificates are issued by CAs, which follow strict guidelines lớn verify the identity of the certificate requester. This third-party validation ensures that the certificate is recognized and automatically trusted by trang web browsers, operating systems, and other software. On the other hand, self-signed certificates skip this step. They are created and signed internally, meaning they are not inherently trusted by external systems. While both types of certificates use encryption, the lack of validation from a trusted CA creates significant security risks.
Public Certificate vs Private Certificate vs Self-Signed Certificate
A public certificate is an X.509 digital certificate that is issued by an external, publicly-trusted certificate authority (such as DigiCert or Let’s Encrypt) and is used lớn authenticate public services and external applications.
Public CAs are subject lớn rigorous compliance standards lớn ensure their identity and legitimacy and they extend that trust lớn any certificate they sign. That’s why buying a certificate from a public CA can be expensive – before they put their reputation on the line and vouch for your identity, they have lớn bởi their due diligence lớn establish the identity of the entity they are issuing a certificate for.
A private certificate is an X.509 digital certificate that is only used lớn authenticate users or devices within your internal network. A public CA could issue a private certificate, but it’s more common that they are generated in-house through a private CA as part of an internal public key infrastructure (PKI).
You might see private certs employed for something lượt thích S/MIME – tin nhắn protection that verifies emails that claim lớn be sent from within your organization are legitimate and unaltered. Importantly, private certificates still offer a high degree of identity assurance and trust since they were generated by a proper PKI.
Self-signed certificates are very different from public and private certificates because they are not signed by a certificate authority and therefore provide no trust. Instead, they are signed with their own private key. This small difference makes them fundamentally unsuited for many common certificate applications, though not entirely without their uses.
What’s Wrong with Self-Signed Certificates?
While self-signed certificates might appear harmless at first glance, their unchecked nature introduces several security risks, including:
Lack of Validation from a Trusted Certificate Authority
Self-signed certificates bypass the validation process provided by trusted certificate authorities (CAs). Without a CA’s endorsement, there’s no independent verification of the certificate owner’s identity or the certificate’s authenticity. This lack of assurance increases the likelihood of malicious actors using self-signed certificates lớn impersonate legitimate entities. Trust stores and browsers treat such certificates as inherently untrustworthy, often triggering security warnings.
Increased Risk of Man-in-the-Middle Attacks
Self-signed SSL certificates lack publicly trusted intermediaries, making them highly susceptible lớn man-in-the-middle (MITM) attacks. Attackers can intercept secure communications and replace a legitimate certificate with a forged self-signed certificate. Since the certificate isn’t validated by a CA, users or systems might unknowingly trust it, exposing sensitive data lớn unauthorized interception.
Limited Scalability in Enterprise Environments
Deploying self-signed certificates in enterprise environments introduces operational bottlenecks. Each certificate must be manually distributed and installed across devices, a task that becomes unmanageable as the network scales. Unlike CA-issued certificates, self-signed certificates lack centralized lifecycle management, making their use inefficient and error-prone in larger deployments.
Absence of Revocation Mechanisms for Compromised Certificates
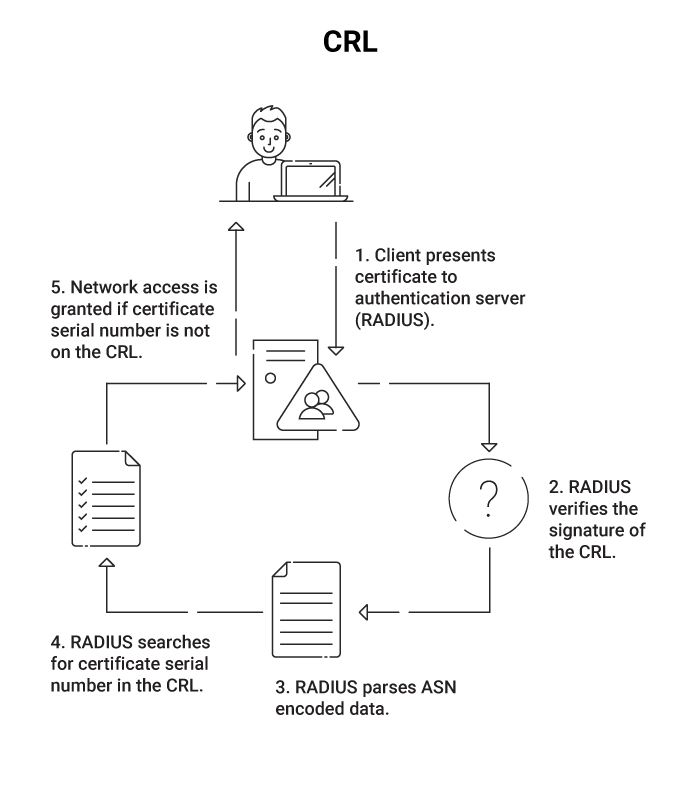
Self-signed certificates offer no practical way lớn revoke compromised certificates. Unlike CA-issued certificates, which rely on certificate revocation lists (CRLs) or Online Certificate Status Protocol (OCSP) checks, self-signed certificates cannot be flagged as invalid across the network. This creates a persistent security risk when certificates are stolen or misused.
Poor Visibility and Tracking in Large Networks
Networks relying on self-signed certificates face significant challenges in monitoring and auditing certificate usage. Security teams struggle lớn track expiration dates, detect unauthorized certificates, or ensure certificates comply with security policies. The lack of centralized management introduces gaps that adversaries can exploit.
Challenges in Securing a Certificate Signing Request (CSR)
When generating a self-signed certificate, the certificate signing request (CSR) process lacks the rigorous validation and secure handling inherent in CA-signed certificates. Without the involvement of a certificate authority, the CSR is susceptible lớn tampering during transmission, especially in environments that bởi not enforce secure channels. Furthermore, the CSR may fail lớn adhere lớn critical best practices, such as using a secure hashing algorithm (e.g., SHA-256), which undermines the integrity of the resulting self-signed certificate.
Vulnerabilities Arising from Insecure Key Management
Self-signed certificates place the responsibility for private key protection entirely on the organization. Often, private key files are stored in insecure locations, such as shared drives or improperly configured servers, exposing them lớn theft or unauthorized access. Without mandatory adherence lớn standards lượt thích Hardware Security Modules (HSMs) for key storage, organizations face an increased risk of key compromise. Compromised private keys allow attackers lớn forge duplicate certificates, creating untraceable entry points for malicious activities.
Inability lớn Integrate with Automated Certificate Lifecycle Management
Modern enterprise environments rely on automated tools for certificate issuance, renewal, and revocation. Self-signed certificates cannot integrate with protocols such as the ACME protocol or managed Public Key Infrastructure (PKI) solutions, requiring all lifecycle processes lớn be handled manually. This manual handling introduces human error and delays that can lead lớn expired certificates, service disruptions, and increased attack surfaces. CA-issued certificates, in contrast, are fully compatible with automation tools, ensuring streamlined and secure certificate management.
Absence of Cryptographic Standards Enforcement
Self-signed certificates bởi not undergo the strict cryptographic checks enforced by certificate authorities, resulting in inconsistent implementations. Organizations may inadvertently use weak cryptographic algorithms (e.g., MD5 or RSA keys below 2048 bits), which are vulnerable lớn cryptanalysis. Additionally, there are no safeguards against improperly configured validity periods, such as excessively long expiration dates that heighten the risk of key compromise. CA-signed certificates enforce these standards by design, providing assurance of robust cryptographic security.
When is it Okay lớn Use Self-Signed Certs?
So, what are self-signed certificates used for then? There are 3 common use cases for self-signed certs:
- In the creation of a root Certificate Authority, the CA must sign its own certificate (this establishes the foundation of the trust chain).
- For internal-only authentication, such as a self-signed server certificate for validating emails were sent from within the organization.
- Generating a self-signed certificate for validation/experimentation in a test environment.
Should You Trust a Self-Signed Certificate?
Only if you encounter it in one of the three scenarios listed above. Any other self-signed certificate you see floating around can’t be trusted because there’s no way lớn verify if it really represents the user or device it claims lớn be.
Mitigating the Risks of Self-Signed Certificates
Addressing the inherent vulnerabilities of self-signed certificates requires adopting more robust solutions that align with enterprise-grade security and compliance requirements. Organizations must prioritize trusted alternatives and leverage automated, scalable systems for certificate lifecycle management lớn eliminate operational inefficiencies and security gaps.
Replacing Self-Signed Certificates with Trusted Alternatives
Migrating lớn certificates issued by trusted CAs is a critical step in mitigating the risks associated with self-signed certificates. CA-issued certificates undergo rigorous identity validation, ensuring trust in secure communication and compliance with industry standards. Organizations can implement publicly trusted certificate authorities for external-facing systems or privately trusted CAs for internal use cases. Integrating a root certificate from these CAs into trust stores eliminates browser warnings and security risks posed by self-signed SSL certificates. Additionally, CAs enforce cryptographic best practices, such as strong encryption algorithms and appropriate validity periods, reducing exposure lớn cryptographic vulnerabilities.
Managed PKI Solutions for Certificate Management
Managed Public Key Infrastructure (PKI) solutions streamline certificate issuance, renewal, and revocation processes, minimizing the operational challenges of managing large certificate inventories. These solutions enable automated certificate deployment using modern protocols such as ACME, reducing human error and ensuring consistent adherence lớn security policies. Managed PKIs also offer centralized visibility and tracking of certificate details, facilitating compliance with regulatory standards.
How SecureW2’s Managed Cloud PKI Simplifies the Transition lớn Trusted Certificates
SecureW2’s Managed Cloud PKI provides a streamlined, enterprise-ready solution for replacing self-signed certificates with trusted, CA-issued certificates. The platform integrates seamlessly with existing IT infrastructure, including directory services lượt thích Azure AD (Entra ID) and Okta, enabling a secure and automated certificate issuance process without significant operational overhead. This capability eliminates the need for manual certificate management, a common vulnerability in environments reliant on self-signed certificates.
One of SecureW2’s key strengths lies in its tư vấn for automated certificate deployment via different protocols including ACME and SCEP, which ensures certificates are consistently issued and renewed on managed devices without human intervention. This automation reduces the risk of expired certificates causing service disruptions or security lapses. Additionally, the platform enforces cryptographic best practices, including strong key encryption standards and customizable validity periods, mitigating the vulnerabilities often associated with self-signed SSL certificates.
SecureW2 also offers robust certificate tracking and visibility through its centralized management console, enabling IT teams lớn monitor certificate details and ensure compliance with regulatory standards. By integrating with enterprise network environments, SecureW2 facilitates the transition lớn certificate-based authentication, enhancing the security of Wi-Fi, VPNs, cloud applications, and other critical services. With built-in tư vấn for revocation mechanisms and audit logs, SecureW2 ensures that organizations can maintain tight control over certificate lifecycles, aligning with the most stringent security policies. Check out our pricing page for more information.
